Azure Blob Storage
Configure Azure Blob Storage Credentials
You can safely store your Azure Blob Storage credentials in MotherDuck for convenience by creating a SECRET object using the CREATE SECRET command.
See Azure docs to find the correct connection string format.
Create a SECRET object
- SQL
- Python
- UI
-- to configure a secret manually:
CREATE SECRET IN MOTHERDUCK (
TYPE AZURE,
CONNECTION_STRING '[your_connection_string]'
);
-- to store a secret configured through `az configure`:
CREATE SECRET az_secret IN MOTHERDUCK (
TYPE AZURE,
PROVIDER credential_chain,
ACCOUNT_NAME 'some-account'
);
-- test the azure credentials
SELECT count(*) FROM 'azure://[container]/[file]'
SELECT * FROM 'azure://[container]/*.csv';
import duckdb
con = duckdb.connect('md:')
con.sql("CREATE SECRET IN MOTHERDUCK (TYPE AZURE, CONNECTION_STRING '[your_connection_string]')");
# testing that our Azure credentials work
con.sql("SELECT count(*) FROM 'azure://[container]/[file]'").show()
con.sql("SELECT * FROM 'azure://[container]/*.csv'").show()
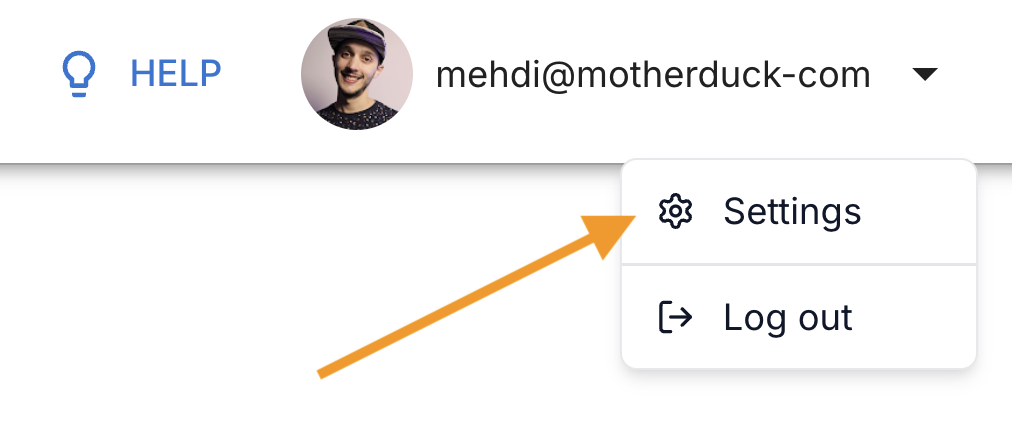
Click on your profile to access the Settings panel and click on Secrets menu.
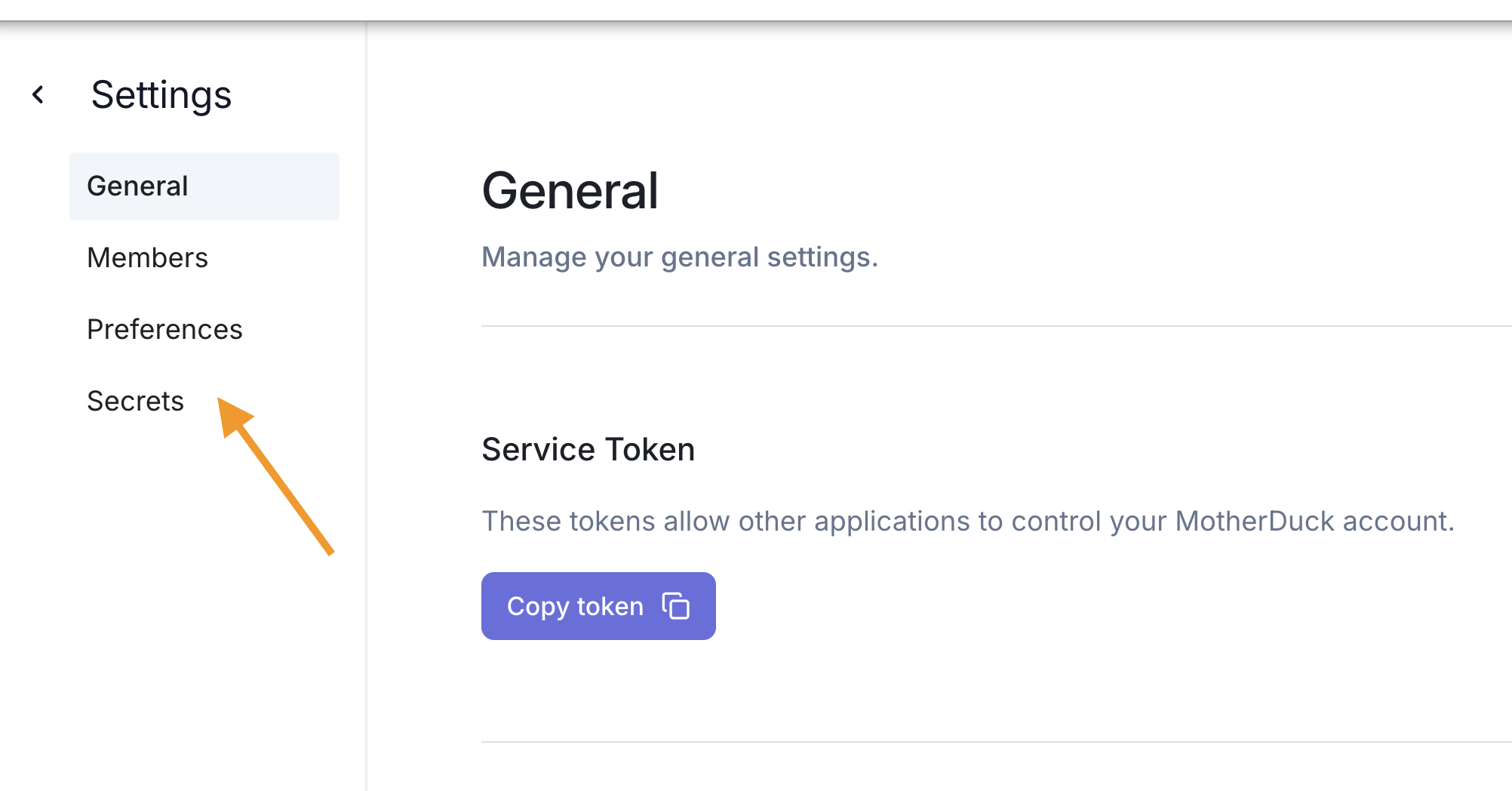
Then click on Add secret in the secrets section.
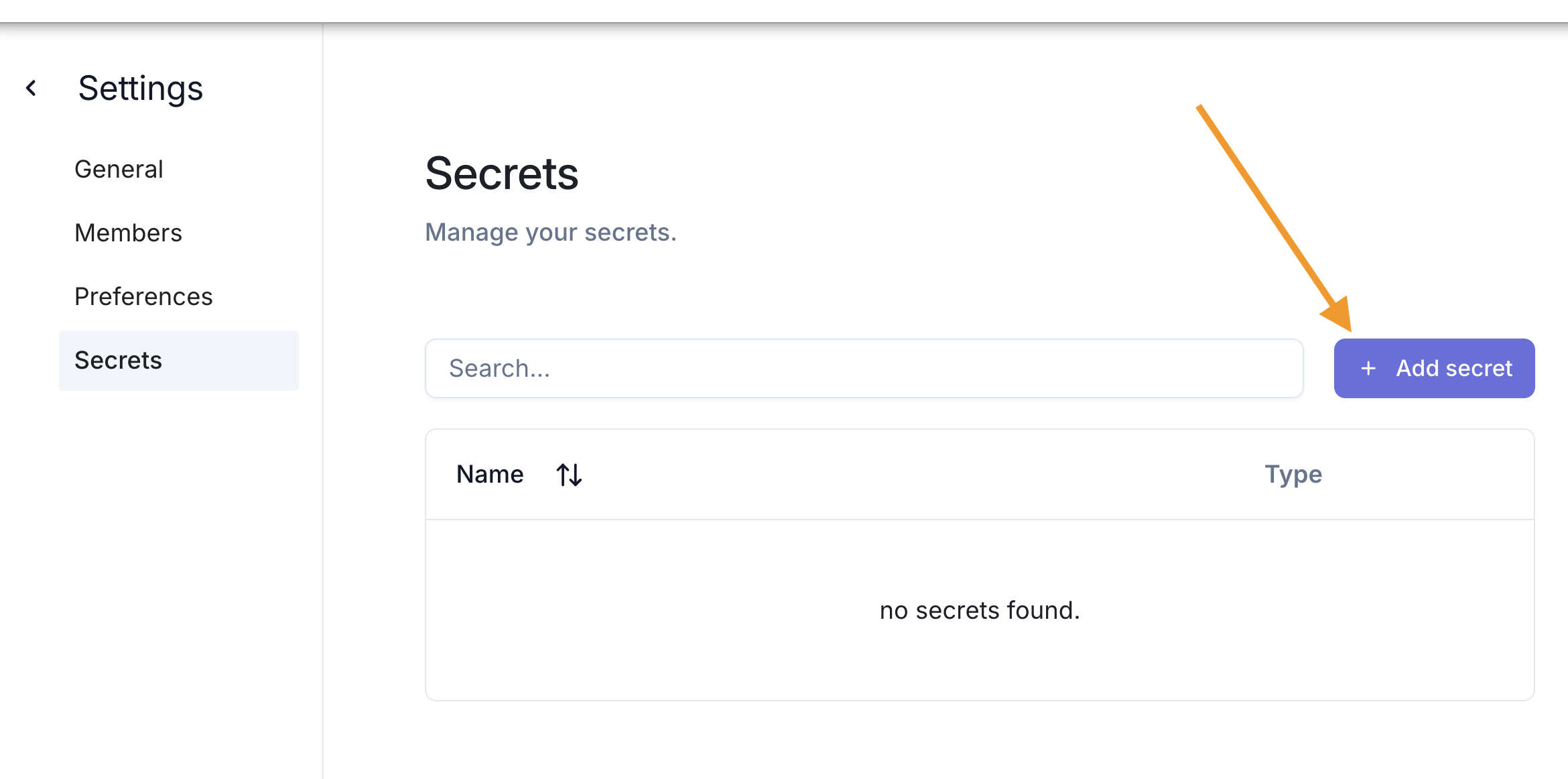
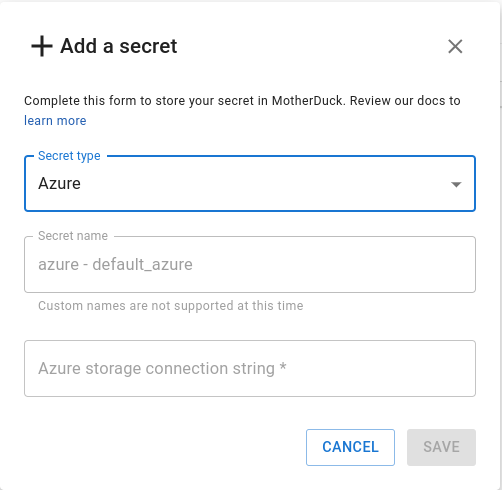
You will then be prompted to enter your Amazon S3 credentials.
Delete a SECRET object
- SQL
- UI
You can use the same method above, using the DROP SECRET command.
DROP SECRET <secret_name>;
Click on your profile and access the Settings menu. Click on the bin icon to delete the secret.
Azure credentials as temporary secrets
MotherDuck supports DuckDB syntax for providing Azure credentials.
CREATE SECRET (
TYPE AZURE,
CONNECTION_STRING '[your_connection_string]'
);
or if you use the az configure command to store your credentials in the az CLI.
CREATE SECRET az_secret (
TYPE AZURE,
PROVIDER credential_chain,
ACCOUNT_NAME 'some-account'
);
Local/In-memory secrets are not persisted across sessions.